How to find OPTIONS method Enable Vulnerability
Today we are going to Learn various techniques to find OPTIONS Method Enable in Web-Application. To find HTTP Protocol methods and the tools used to extract those available HTTP methods in a web server. The HTTP protocol comprises of a number of methods that can be utilized to not only gather the information from the Web server but can also perform specific actions on the Web server. These techniques and methods are helpful for web application developers in the deployment and testing stage of web applications.
GET and POST is the most well-known methods that are used to access and submit the information provided by a web server, respectively. HTTP Protocol allows various other methods as well, like PUT, CONNECT, TRACE, HEAD, DELETE. These methods can be used for malicious purposes if the webserver is left misconfigured and hence poses a major security risk for the web application, as this could allow an attacker to modify the files stored on the webserver.
OPTIONS: The OPTIONS method is used to request the available HTTP methods on a web server.
GET: GET request is the most common and widely used method for websites. This method is used to retrieve the data from the Web server for a specific resource. As the GET method only requests for the data and doesn’t modify the content of any resources, it’s considered to be safe.
POST: POST requests are used to send (or submit) the data to the Web server to create or update a resource. The information sent is stored in the request body of the HTTP request and processed further. An example illustrating the same is the “Contact us” form page on a website. When we fill a form and submit it, the input data is then stored in the response body of the request and sent across to the server.
PUT: The PUT method allows the end-user (client) to upload new files on the Web server. An attacker can exploit it by uploading malicious files or by using the victim’s server as a file repository.
CONNECT: The CONNECT method could allow a client to use the web server as a proxy.
TRACE: This method echoes back to the client, the same string which has been sent across to the server, and is used mainly for debugging purposes.
HEAD: The HEAD method is almost similar to GET, however without the message-body in the response. In other words, if the HTTP request GET /products return a list of products, then the HEAD /products will trigger a similar HTTP request, however, won’t retrieve the list of products.
DELETE: This method enables a client to delete a file on the Web server. An attacker can exploit it as a very simple and direct way to deface a Web site or to perform a DoS attack.
Now let us use some tools to identify the HTTP methods enabled or supported by the Web server.
- cURL
- Nikto
- Nmap
- Nmap Automator
- Netcat
- Burpsuite
The cURL is a command-line tool to get or send the data using the URL syntax and is compatible with various well-known protocols (HTTPS, FTP, SCP, LDAP, Telnet etc.) along with command line (CLI) options for performing various tasks (Eg: User authentication, FTP uploading, SSL connections etc). The cURL utility by default comes installed in most of the distributions. However in case, cURL is not installed, then we can install the same via apt-get install curl command. For more details refer to Below URL.
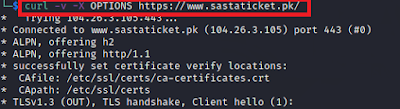
Through the cURL command we can identify the HTTP Options available on the target URL as follows:
curl -v -X OPTIONS IP address or site name
Nikto
Nikto is a Web server scanner that tests Web servers for dangerous files/CGIs, outdated server software and other issues. It performs generic and server types of specific checks.
Through the Nikto command we can identify the HTTP Options available on the target URL as follows:
nikto -h IP address or site name
Nmap is a free and open-source security scanner, used to discover hosts and services on the network. This is another method of checking which HTTP methods are enabled by using an NMAP script called http-methods.nse, which can be obtained from https://nmap.org/nsedoc/scripts/http-methods.html.
Let us use NMAP command to enumerate all of the HTTP methods supported by a web server on the target URL as follows :
nmap --script http-methods IP address or site name
OR
nmap --script http-methods --script-args http-methods.url-path='/website' <IP address>